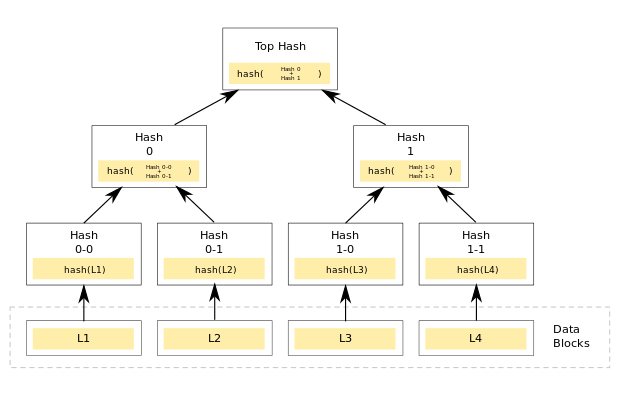
If using buildroot or Yocto to build a Linux distro, a container environment might be used as build environment. Within the container the privileged kernel operations may be blocked, so creating device-mapper crypto-devices or Loopback-Devices is not possible.
Therefor, creating an encrypted file system within contained requires a special work flow; demonstrated by following github repository.
https://github.com/frehberg/cryptsetup-containerized
First the demonstrator is creating a container image, containing the required command line tools. Later this container is used for the following two stages:
- Within the container a plain ext4 image file is created using the content folder
./tar/. - Finally the container is used to encrypt the image file
tmp/images/rootfs.img. This step does not required extended container privileges.
The test script ./test-efs-privileged.sh can be used to validate the encrypted image file. The test script requires root/sudo privileges on the host.
Note: The folder ./tar/ contains the directories and files of the image in question. The content of the encrypted file system may not be altered afterwards without extended container privileges.